Podcast: Play in new window | Download
Subscribe: Apple Podcasts | RSS
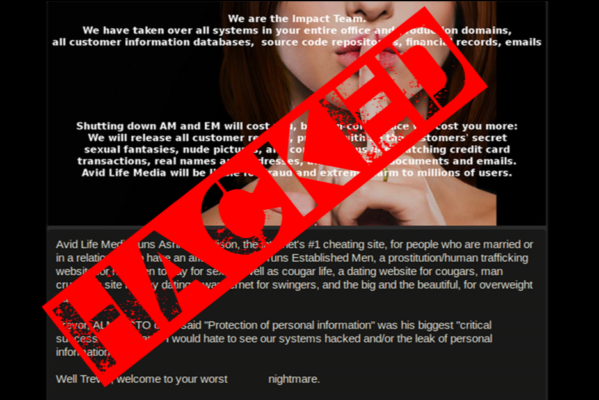
[headline tag=”div” css_class=”h2″ color=”color2″]Story: Ashley Madison (2:00)[/headline]In August of 2015, Avid Life Media received a stunning ultimatum from some unknown hackers to shut down various sites after having breached the controversial cheating site Ashley Madison or face the concequences of having tens of gigabytes of customer information, source code, company emails and other sensitive data be released to the public. Little to nothing was known about the team of hackers only known by “Impact Team” insinuating that there was more than one hacker.
However, an investigation by renown security expert Brian Krebs uncovered a particular twitter account that might reveal possible nuggets of truth about who is “Impact Team”. Who is Thadeus Zu and is he Impact Team or part of them? After Brian discovered a twitter user by the name of “Thadeus Zu” had tweeted links to the hacked data before it was known to the public, and exclusively given to Krebs by someone directly or closely involved in the hack, Brian set out to see what other information could be uncovered about this person operating under the pseudonym “Thadeus Zu”.
[section_headline tag=”h3″ lined=”yes” color=”color2″]Sources:[/section_headline] [list type=”minus” color=”color1″] [/list][headline tag=”div” css_class=”h2″ color=”color2″]The Burning Question (16:30)[/headline]
Unlike many company breaches that disclose poor user credentials storage practices, source code behind Ashley Madison revealed that they did implement a fairly secure password storage process using Bcrypt. However, it was a side channel of the user credential storage process that allowed researchers to crack 10% of the 36 million passwords within 1 month of the breach with a high possibility that more or the remaining will be cracked as well.
[section_headline tag=”h3″ lined=”yes” color=”color2″]Question[/section_headline][section_headline tag=”h3″ lined=”yes” color=”color2″]Answer:[/section_headline]What is the proper way for storing password in your application?
Though there has been much written and discussed about proper password storage for developers, when distilled down to its basics, there are 3 important factors:
1. Strong cryptographic hash algorithm
There are less than secure hashing algorithms such as MD5 and the once popular Secure Hashing Algorithm 1 (SHA1) algorithm that has fallen out of favor for the more secure SHA2 family (SHA-224, SHA-256, SHA-384, SHA-512).
However, despite the strength of a strong cryptographic hashing algorithm, with today’s hardware capabilities, Moore’s law and raw ingenuity, a strong algorithm isn’t enough.
2. Time – Key derivation function (specifically a password based key derivation function )
A password based key derivation function is an additional layer that encompasses a strong cryptographic hashing algorithm that additional fortitude to the process. With the ever growing hardware capabilities that allows on-the-fly brute force of passwords, one of the few weapons on your side is time. Password based key derivation functions provide that weapon by putting a password hashing computation through N number of rounds of hashing (where N is a configured number of rounds e.g. 86,000). Inevitably, in order for an attacker to successfully crack a password through brute force would also require performing the same number of rounds of hashing and forced to adhere to the laws of time.
Unfortunately, with Moore’s Law, hardware speeds and rig configuration for parallel computation, there is one more ingredient that lends itself to ensure that Time is not on the side of an attacker.
3. Good password requirements
Great password criteria such as upper and lower case characters, numbers and special characters is only a fraction of what goes into good passwords. But also, the ability to remember a password, which is why pass-phrases are king. Such as “Lucy in the sky with d1amonds!” is allot easier to remember than PK%(hdl1_9r). However, there is a astronomical difference between even 10 character and a 12 character password. Using something like GRC password crack checker to see exactly what we are talking in the way of “Time” that it would possibly take an attacker to crack a password.
Therefore, while you have control over what password storage process you use to store user’s passwords of your application, you also have control over what password requirements you want to enforce your users to abide by. Because at the end of the day, most likely, great password storage can usually be a last line of defense where attackers have circumvented another area of your application to gain access your application’s users.
[section_headline tag=”h3″ lined=”yes” color=”color2″]Source:[/section_headline] [list type=”minus” color=”color1″] [/list][headline tag=”div” css_class=”h2″ color=”color2″]Fab Failure (22:25)[/headline] Many of you are familiar and have probably used repository hosting companies such as GitHub and Bitbucket. But could you imagine them being compromised to the point that customers lost data, reputations were shot and an inability to recover was imminent? Well that is exactly what happened to the up and coming Code Space when a lack of a sufficient backup plan and their AWS cloud account was compromised.
Sources:
[list type=”minus” color=”color1″]- CSO Online – Code Spaces Forced to cLose its Doors
- Network Computing – Code Spaces a Lesson in Cloud Backup
[Music Credits]
music by audionautix.com
