Podcast: Play in new window | Download
Subscribe: Apple Podcasts | RSS
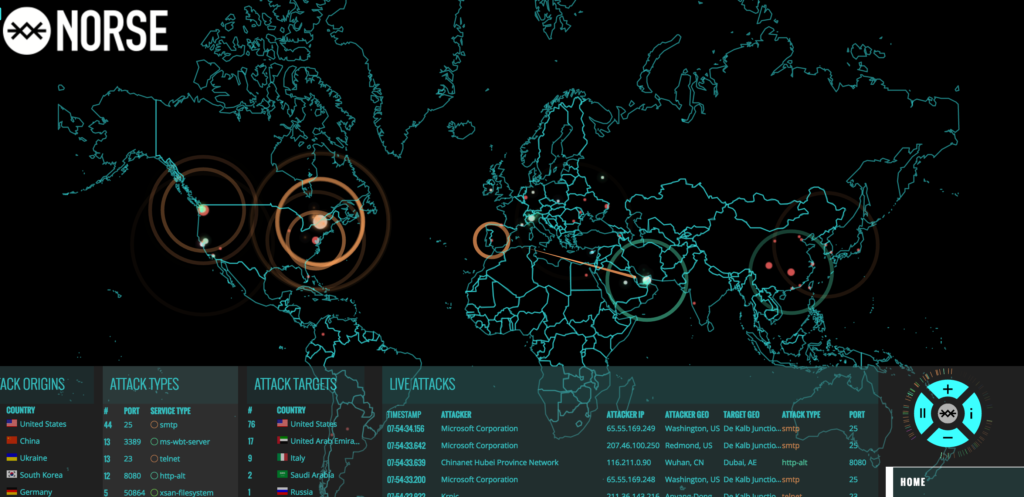
Story: DDoS History as a Cyber Weapon
Like so many advancements in human history, they often have a tendency to be used for more than what the originator had conceived. The internet provides a vast amount of various beneficial services. Yet, those same services are often besieged by those that weld the collective power of the internet to conduct distributed denial of service attacks. In this story, we look at the DDoS history and its impact as a cyber weapon.
 For over the past 60 years, we have seen numerous movies showcase the idea of a weapon weld the ability to flash an invisible wave of power that could knock some opposition’s computer or electronic system offline. Sometimes it’s in the form of a futuristic pistol generating pulses or a kill switch as in the ship Nebuchadnezzar in the movie Matrix.
For over the past 60 years, we have seen numerous movies showcase the idea of a weapon weld the ability to flash an invisible wave of power that could knock some opposition’s computer or electronic system offline. Sometimes it’s in the form of a futuristic pistol generating pulses or a kill switch as in the ship Nebuchadnezzar in the movie Matrix.
Back to earth, we have seen this force in reality starting with the nuclear bomb test blasts that the U.S. has recorded for half century. The electromagnetic pulse effect of such detonations in the megatons at various altitudes have shown to have a powerful effect. As we’ll see in the podcast, ramifications from those nuclear blast tests have been felt at places like Hawaii where businesses and services have been knocked offline.
In all of these examples, the results are the form of a denial of service. Where a service has been rendered unavailable. With the collective nature of the internet, we have seen the effective power of forcing a network, site or service offline due to denial of service attacks. This is especially evident when the attacking power is distributed over numerous computer resources such as we seen provided by the botnets formed from the Zeus Trojan.
In this first part, we’ll examine DDoS history (distributed denial of service) and its role that it has played over the last two and half decades. From the origins of nothing more than juvenile uses to take over chat networks to military weapons used to take down entire nations. Like the cyber weapon we saw in the story on Stuxnet, DDoS attacks have shown to be a viable private and state-level weapons used to for extortion, smoke screens or military pre-strike attacks.
Fabulous Failure
 In natural for most people and society to hear about the benefits of an education. In this fabulous failure we’re here about the story of hackers how have managed to circumvent the network of the Central Bank of Bangladesh. But despite holding all the chips, education or possibly a lack of, causes them to loose out on $700 million.
In natural for most people and society to hear about the benefits of an education. In this fabulous failure we’re here about the story of hackers how have managed to circumvent the network of the Central Bank of Bangladesh. But despite holding all the chips, education or possibly a lack of, causes them to loose out on $700 million.