Now Microsoft Azure offers a vast and varying array of Cloud services, many of which provide different ways to process and exchange data. Many of you might already be leveraging Azure’s various Storage services in your website or desktop app or one of their messaging bus options for exchanging data between mobile and IoT devices. But whether you are already working with Azure or considering utilizing some of their services, a fundamental and important question that you should asking is: “how do I protect my data?”.
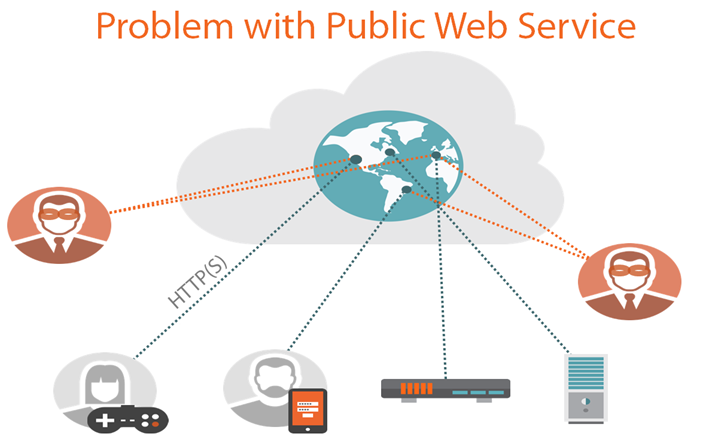
Every type of application faces a vast number of security risks, whether that is a web, cloud or enterprise applications. Take applications that are exposed to the public such as public facing web services or applications for instance, the ability for anyone to attempt to interact with that service or application is a real threat. There can be many reasons and goals behind a user’s malicious activity, but one prized area is access to your data. When we start talking about storing that data in a cloud providers services such as Microsoft Azure, that data becomes resources that could be directly accessible depending on your applications needs. Protecting that data should be a first priority and Azure’s Shared Access Signatures helps add that strong layer of security for your applications data.
I have talked about Microsoft Azure’s Shared Access Signatures before to a small extent as well as when talking about specific Azure services such as Blob and Table storage as well as with Service Bus. But, I haven’t dived to the depth and cover such a wide breadth of how to use them and the security concerns they address as in my new Pluralsight course: Getting Started with Microsoft Azure’s Shared Access Signatures.
Getting Started with Microsoft Azure’s Shared Access Signatures
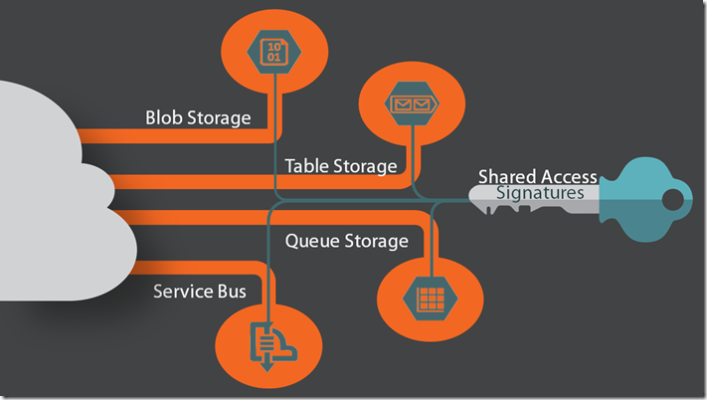
Microsoft Azure’s Shared Access Signatures is Azure’s out-of-the-box security access control, providing a uniform way of granting granular access to data across a wide range of Azure services.
Now, you can learn how to leverage Azure’s resource security control “Shared Access Signatures” on a vast range of supporting services including Blob, Table and Queue Storage services as well as their messaging bus based services such as Service Bus, Notification and Event hubs. Using real-world applications such as the web client of a distributed application, I demonstrate how Shared Access Signatures can be used to secure Azure resources and enforce security best practices. So whether you’re a seasoned Microsoft Azure developer or just considering them for your next cloud project, come learn how you can consider security in your next cloud leveraging application right out the gate.
Pluralsight is one of the leading providers of online technical course by top industry leaders. If there is a technical subject matter you’re interested in, most likely they’ll have it in their world’s largest online course catalog. In addition, they also supply a 10 day free trial and make it even easier to take them for a spin and check out courses of interest.
One of the biggest growing areas of software development, is companies leveraging the cloud in their applications. However, the number one reason why companies that aren’t leveraging the cloud is security. I wanted to develop a course that spoke both to the novice as well as the seasoned developer of security risks and how their cloud application could be vulnerable. This course is aimed at helping the community of Azure developers be cognitive as well as capable of implementing a strong layer of security in the existing or next cloud application and Shared Access Signatures can help them do just that and I hope Getting Started with Microsoft Azure’s Shared Access Signatures will help you too.