Since its creation in 2009, Node.js has seen exponential growth in its popularity as well as its surrounding community of users and the applications they are building. With the drive towards a connected society, the need for web applications has never been greater. So many top name companies such as Wall Street Journal, eBay, GoDaddy, Microsoft and Ancestry.com have embraced Node.js for various needs.
Web Development and the Current Times…
 Yet, despite the push to connect the world as we know it, businesses of all sizes fall victim to data breaches everyday. With over 5,000 data breaches reported since 2005, more than 50% occurred in the last 5 years, we clearly still have a problem. Web application security isn’t going anywhere and it isn’t getting any easier to securely host user personal and financial information.
Yet, despite the push to connect the world as we know it, businesses of all sizes fall victim to data breaches everyday. With over 5,000 data breaches reported since 2005, more than 50% occurred in the last 5 years, we clearly still have a problem. Web application security isn’t going anywhere and it isn’t getting any easier to securely host user personal and financial information.
The underlying reasons for these data breaches plague every web application despite the technology stack on which they were built. However, just like any platform or framework, the technical details behind the various mitigations are different. With the popularity of Node.js continuing to skyrocket, understanding how to specifically mitigate security threats a Node.js web application will face is exactly what I help developers with in my new Pluralsight course Securing Your Node.js Web Application (watch “Course Overview” for a sneak peek).
The Course
In the module on Proper User Authentication we not only tackle the obvious user password storage but we also look at the impact of password composition and how to enforce rules regarding user passwords requirements. But if that isn’t enough, we also deep-dive into a number of brute force safeguards such as login delays, temporary bans and tracking logins.
The popular term stateless has continued to show up in stateless components and stateless authentication. But the truth is that modern web applications are highly stateful systems with an endless list of user information used to make the user experience as delightful as ever. Therefore, the module on Session Management takes developers through the process of utilizing the code, tools and techniques to provide secure user sessions and mitigate threats such as session hijacking.
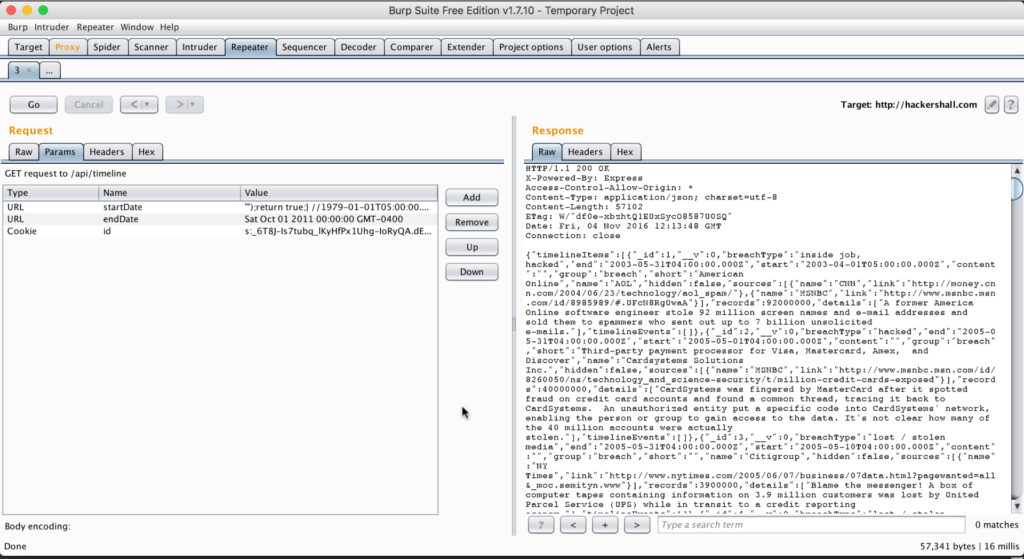
But implementing the necessary code and configuration against mitigations isn’t only part of the battle. Understanding how to test your application for vulnerabilities another part. In Securing MongoDB from Injection Attacks, we start with Burp Suite and how we can utilize it to test for NoSQL injection attacks against the applications MongoDB database. But Burp Suite is only one of the tools we’ll use, we’ll also look at a variety of other industry standard security testing tools along the way such as Netsparker and OWASP’s own Zed Attack Proxy.
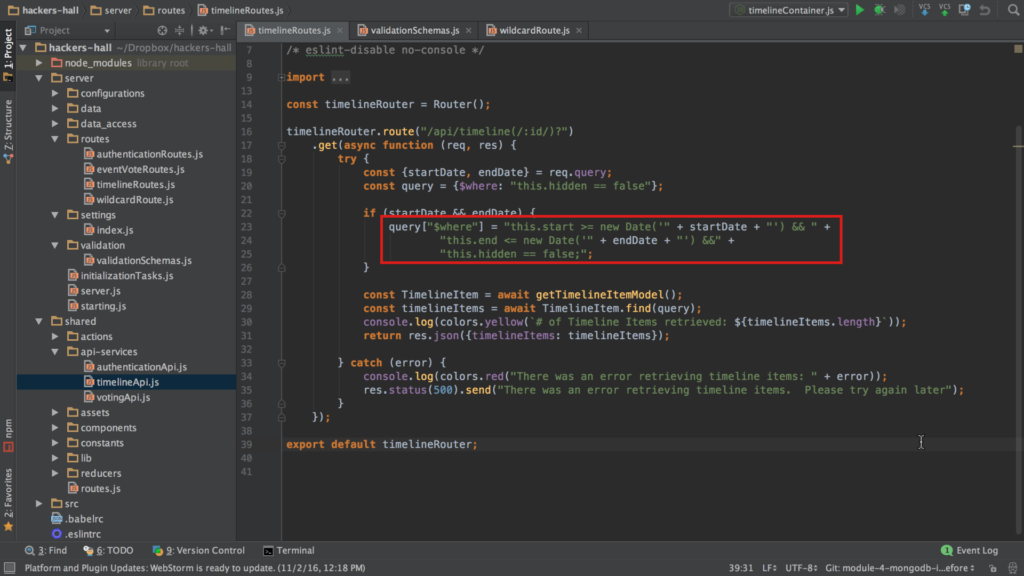
Another frightening developer conundrum that I know I am guilty of and have witness on numerous occasions, that single, fully privileged database access account that the application utilizes. How many of you have worked on a project where there is a single account used by the application to interact with your MongoDB database? That’s one of a number of function-level access control issues we tackle in the Access Control module.
Serving your Node.js web application over HTTPS and implementing security measures such as the use of Content-Security Policies (CSP) and HTTP Strict Transport Security (HSTS) is another area we cover in the module on Securing Our Connection. Along with the module Defending Against Cross-site Scripting Attacks where we look at a number of mitigation techniques at our disposal.
Hackers Hall
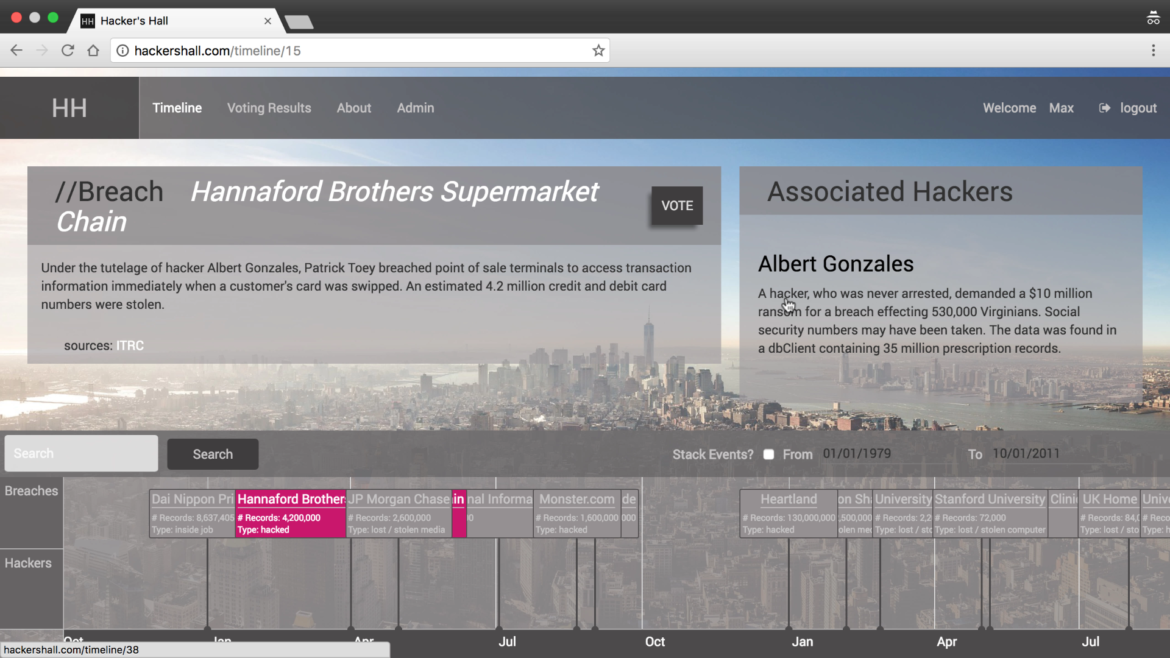
While navigating through the modules, implement the necessary code, deep-dive into the security threats and exploiting them using a number of security tools, we’ll do it all against a React.js / Node.js application called Hacker’s Hall. So, you’ll have a working context to use to follow along.
I set out in this course not only help Node.js developers build more secure web applications through the specific coding examples, but also leave them with the knowledge to make secure architectural decisions, expand their approaches and the tools to test their applications. It was a long time in the making Securing Your Node.js Web Application, and I hope it benefits you on your existing or future Node.js project.